Security in the GSM system
Helen Li
SMQT
2016-06-06 14:33:51
Security in the GSM system
As a result of recent mainstream controversy involving David Beckham’s alleged text messages, some articles have been published criticizing GSM’s security, even though it is highly unlikely in this case that any messages were in fact intercepted over the radio link (if at all). As a result of some of these articles, I have decided to publish a technical article dealing with only the facts of how security measures are implemented in the GSM system, the world’s most commonly used mobile telephony system. There is also a section summarizing the known flaws in these measures, and what has been done in subsequent revisions of the standard (i.e. by 3GPP) to resolve them.
Security features offered by GSM
GSM specification 02.09 identifies three areas of security that are addressed by GSM. - Authentication of a user – this deals with the ability for a mobile phone to prove that it has access to a particular account with the operator - Data and signaling confidentiality – this requires that all signaling and user data (such as text messages and speech) are protected against interception by means of ciphering - Confidentiality of a user – this deals with the fact that when the network needs to address a particular subscriber, or during the authentication process, the unique IMSI (international mobile subscriber identity) should not be disclosed in plaintext (unciphered). This means someone intercepting communications should not be able to learn if a particular mobile user is in the area. These 3 areas are covered in detail below.
Authentication
Authentication
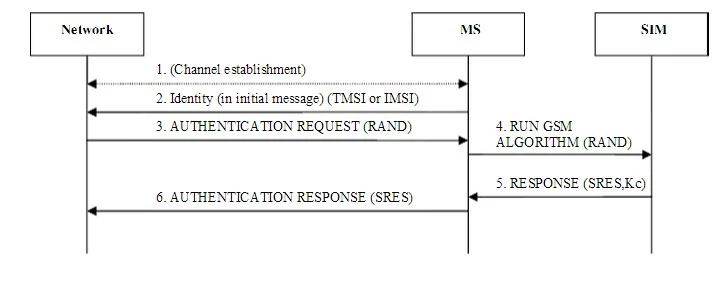
Authentication is needed in a cellular system to prohibit an unauthorized user from logging into the network claiming to be a mobile subscriber. If this were possible, it would be easily possible to “hijack” someone’s account and impersonate that person (or simply making that person pay for the services). In fact, this was possible in some earlier cellular systems. In order to solve this problem, some sort of challenge needs to be issued by the network which the mobile phone (MS) must respond to correctly.
The SIM card
Many users of GSM will be familiar with the SIM (Subscriber Identity Module) – the small smartcard which is inserted into a GSM phone. On its own, the phone has no association with any particular network. The appropriate account with a network is selected by inserting the SIM into the phone. Therefore the SIM card contains all of the details necessary to obtain access to a particular account. These details come down to just 2 items of information. - The IMSI – International Mobile Subscriber Identity – a unique number for every subscriber in the world. It includes information about the home network of the subscriber and the country of issue. This information can be read from the SIM provided there is local access to the SIM (normally protected by a simple PIN code). The IMSI is a sequence of up to 15 decimal digits, the first 5 or 6 of which specify the network and country (i.e. 50501 for Telstra, Australia) - The Ki – the root encryption key. This is a randomly generated 128-bit number allocated to a particular subscriber that seeds the generation of all keys and challenges used in the GSM system. The Ki is highly protected, and is only known in the SIM and the network’s AuC (Authentication Centre). The phone itself never learns of the Ki, and simply feeds the SIM the information it needs to know to perform the authentication or generate ciphering keys. Authentication and key generation is performed in the SIM, which is possible because the SIM is an intelligent device with a microprocessor.
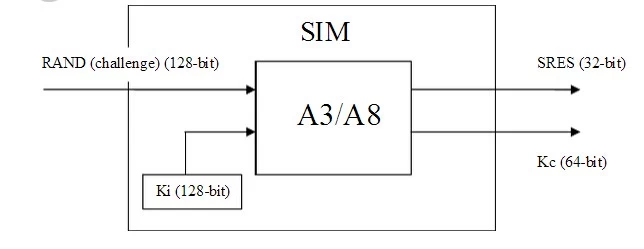
Additional local security in the SIM
The SIM itself is protected by an optional PIN, much like an ATM PIN protects your ATM card. The PIN is entered on the phone’s keypad, and passed to the SIM for verification. If the code does not match with the PIN stored by the SIM, the SIM informs the user (via the phone) that code was invalid, and refuses to perform authentication functions until the correct PIN is entered. To further enhance security, the SIM normally “locks out” the PIN after a number of invalid attempts (normally 3). After this, a PUK (PIN UnlocK) code is required to be entered, which must be obtained from the operator. If the PUK is entered incorrectly a number of times (normally 10), the SIM refuses local access to privileged information (and authentication functions) permanently, rendering the SIM useless. The A3 algorithm and authentication procedure
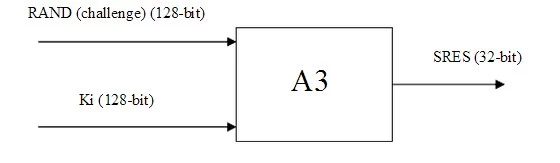
Now that we have established that there is a ‘secret’ Ki known only in the SIM and the network, the authentication procedure simply has to involve the SIM (via the phone) proving knowledge of the Ki. Of course, we could simply submit the Ki to the network for comparison when the network asks for it, but this is highly insecure, since the Ki could be intercepted. Instead, the network generates a 128-bit random number, known as the RAND, which it then uses the A3 algorithm (see figure) to mathematically generate an authentication token known as the SRES. It then sends the RAND to the phone for the phone to do the same. The SIM generates the 32-bit SRES, which is returned to the network for comparison. If the received SRES matches the network’s generated SRES, then the Ki’s Kc (64-bit) Ki (128-bit) must be the same (to a high mathematical probability), and the phone has proved knowledge of the Ki and is thus authenticated.
The RAND must obviously be different every time. Otherwise, if it were the same, an attacker could impersonate the user by sending the same SRES.